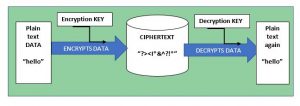
Encryption is a key defense mechanism in your arsenal of defenses to counter attacks and data breaches. Encryption turns easily read plain text data into a format called ciphertext. Ciphertext cannot be read without the means to decode it back to plain text.
Data is encrypted using a cryptosystem –
An algorithm (mathematical function) encodes the data so it is illegible to the human eye.
To read the data again you need a bit key to decode it.
Only authorised users should have this key.
The two main types of encryption methods are Asymmetric and Symmetric cryptosystems. Asymmetric cryptosystems involves using two keys, a public key for doing the encryption and a private key for decoding to read the data. Examples of asymmetric methods are RSA algorithms and AES. Symmetric cryptosystems uses a single private key to both encrypt and decrypt the data. A randomly generated temporary or single use key, known as a session key, keeps data secure during the communication session between two computers. The randomness of generated keys is a good protection against “man-in-the-middle” attacks where a hacker discovers a way to predict and crack your key. Examples of symmetric methods are 3DES and Twofish.
A good rule of thumb to use when selecting an encryption method is “size does matter”! A longer key gives a greater number of possible combinations which makes it a lot more difficult to crack. For some encryption schemes a 256-bit key is enough to dissuade the casual hacker and even enough to withstand the serious hacker using brute force to crack the cipher. For others 2048 is needed to provide equivalent security.
Encryption standards have progressed from DES in the 1970’s to AES the standard of choice presently. DES (Data Encryption Standard) used only one 56-bit encryption key which is now out-dated, whereas, AES uses a block cipher (data is encrypted in lengths called blocks) of 256-bit lengths making it impossibly time-consuming to attempt to crack with current technology. This encryption is one of the most secure encryption standards available at present.
Encryption standards exist and are continually evolving, in an effort, to stay ahead of attackers and their use of increasingly powerful technology. Standards of encryption such as the level of encryption used to protect nuclear weapons could gradually find their way into the business and personal encryption fields. Nuclear style encryption is seen to combine randomness with complex codes to create highly complex keys.
Encryption can be done at any or all levels within an organisation, from individual file level, logical disk drive level, total hard disk encryption, mobile disk level, database and email to network and wifi levels.
However, encryption alone is not enough to protect your critical data. Encryption is only as good as the users who create and use it. Everyone should be aware of the best practices and develop an encryption\recovery policy so as to safely secure and maintain the integrity of their data.
• Use the best option of encryption available to you and use compatible methods of encryption to ensure there are no weak areas in your encryption defences. For example, on a Windows computer use the software disk encryption tool BitLocker with a hardware encryption component a TPM chip. BitLocker encrypts the full hard disk while the TPM chip protects the keys and the boot environment preventing access prior to the disk being available after bootup. Apple computers have FileVault with Apple T2 security chip to do something similar. Microsoft BitLocker Administration and Monitoring (MBAM) interface helps companies use BitLocker encryption policy via the Group Policy and Active Directory. Do not use poor encryption or home made options as this gives you a false sense of being secure when in reality a flawed or poor encryption can be easily hacked.
• Implement an encryption\recovery policy prior to encrypting your machines. Make sure you test it.
• Encryption is a double edged sword. Keeping your key secure is critical. Encrypted, your data is secure and accessible only to authorised personnel with the encryption key, if you lose that key your data is secure and inaccessible even from you. It encrypted properly, it will be impossible to regain assess to your data without your key. A complete restoration of an up-to-date backup is the only guarantee that you will be able to access your data again in this circumstance.
• Have one copy of the encryption key(s) and get your IT provider to certify for you that this is the only copy of the key(s).
• Keep encryption keys safe – very, very safe! It is necessary to encrypt your encryption key too! Never store the key on the same drive, database or app that it encrypted.
• Do not distribute recovery keys freely to users, instead have a recovery policy implemented where selected personnel will use the key to recover a locked computer as needed or alternatively used via Active Directory.
• Use multiple encryption keys – do not have just one encryption key doing all the encryption of your data. Use different keys for different areas of data protection.
• Train your users not to store a USB device containing encryption key in the same place as the computer with the encrypted data when leaving the computer unattended. Microsoft recommend turning off computers rather than leaving them in sleep mode so as to better protect BIOS and boot areas from hacking attempts.
• Change your encryption keys occasionally – tricky to do but can be important in the defense against attacks. It’s harder to hit a moving target!
• Have good backups of all your data in case you cannot decrypt it or corruption occurs. If you are backing up to the cloud ensure that your data is encrypted before you store it in the cloud. If you are creating second disks for a machine as backup ensure the backup disk is created on the same machine with the same TPM or T2 chip otherwise it will not be the same encryption key.
The increase in computing power has enabled attackers to crack poor encryption by brute force, where they use a powerful computer to try different combinations in a continuous stream in the hope of hitting the right one. The more combinations in your encryption method the longer it will take this type of attack to get the right one. Select a tried and tested encryption option, keep up to date with recommended standards, have a good backup and recovery process and never ever give unauthorised access to your key! Robust encryption processes and safeguarding against user error are still the best, and last, lines of defense to help secure you against data breaches and loss.
______________________________________________________________________________________________
If you need advice please don’t hesitate to call one of our qualified engineers. We will be delighted to help.
021-4642096
Business Hours: Monday – Friday 09:00 to 17:30