Many small businesses use security cameras to monitor their premises. As we visit our customers, we often find that such systems have not been sufficiently secured from unauthorised access by outsiders. If you have a security camera system installed and the suppliers have configured the ability to view the cameras remotely, you should really ask yourself if that has been done securely.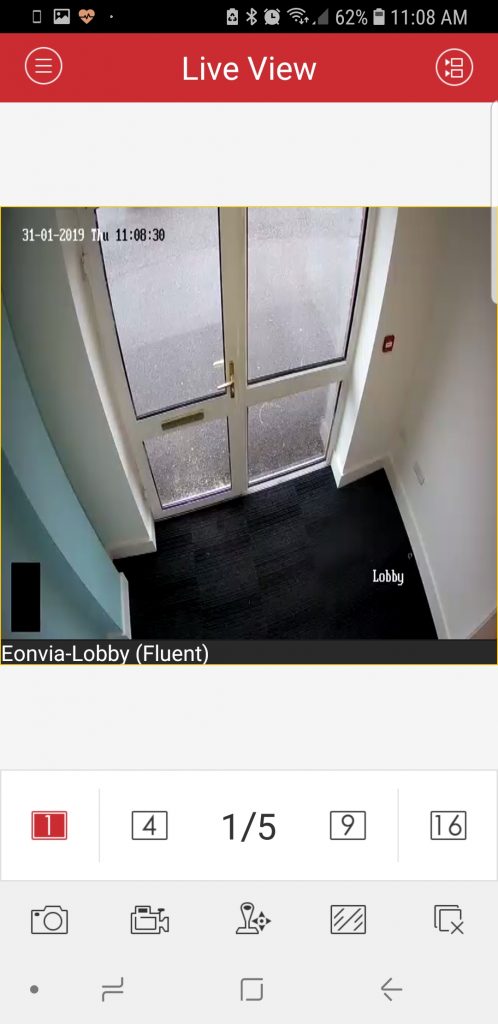
A case in point is a client we recently visited who had a long-established camera system, with the managing director having access to the camera via his phone. When we looked at how this had been set up, we found that the system was using the default “admin” username and only a 4-digit PIN to protect it from outside access. Obviously, this is insufficient security for devices that can reveal whether your site is attended and the patterns of people’s movement.
In other cases, we have found people using cloud based monitoring systems such as hik-connect.com which allows access to many people’s camera system without having to set up firewall rules. In these cases, it is very important to have good, very secure passwords to prevent others from reviewing your camera footage.
If you have a camera system, there are a number of things you should do to provide yourself with basic security for your system.
- Find out what usernames and passwords are active on your system. You don’t want to be a victim like the people described here
- Ensure that only the usernames you need are in place and that the passwords matching those usernames are suitably complex. Try to avoid default usernames such as “admin”. Using such usernames just make the systems much easier to attack.
- Ensure that your camera system is not out of date with existing vulnerabilities. Backdoors and other vulnerabilities are continuously being found and fixed such as this one here. Unfortunately your camera system should not be a “fit and forget” installation. It does need maintenance.
- If you are using a cloud service, make sure that you are comfortable with the risk that someone can hack into that cloud service. There have been multiple examples where cloud services for camera access have be compromised in the past – such as this one.
- If you are serious about security, and you have a sophisticated firewall, you could put further barriers in place to restrict incoming access requests for video. For example, in the past we have set up systems where the users would first connect to VPN(Virtual Private Network) on their firewall before moving on to connect to their camera system.
———————————————————————————-
If you need advice please don’t hesitate to call one of our qualified engineers. We will be delighted to help.
021-4642096
Business Hours: Monday – Friday 09:00 to 17:30